![Updated path to php catalog]()
I needed to upgrade the bundled php-version 6.5.12 to the latest 6.5.14 due to some security vulnerabilities. This is how I upgraded php in XAMPP to the latest version.
- Start by downloading the latest php version. Are you using XAMPP select the Thread Safe zip version
- Unzip the files to a new folder with name php_VERSION under the XAMPP-folder. Example C:\xampp\php_5.6.14
- Stop the Apache service from the XAMPP control panel
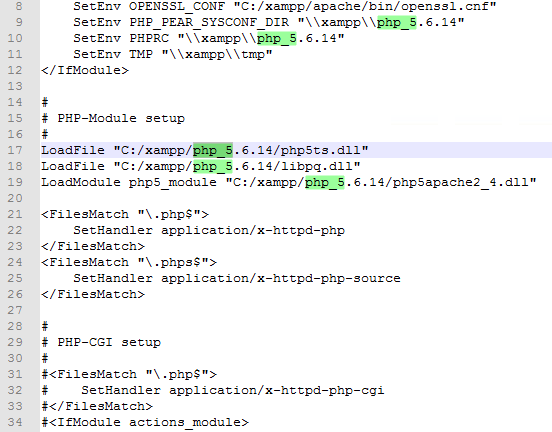
- Backup the file C:\xampp\apache\conf\extra\httpd-xampp.conf
- Open the file C:\xampp\apache\conf\extra\httpd-xampp.conf in Administrator mode and replace all the paths to the old php folder to the new path example: C:/xampp/php_5.6.14/. You can also open the file, do the updates, save it to your desktop and manually copy/paste it to the original destination to overwrite the original file in case you forgot to edit it using Administrator user account.
- Start the Apache service from the XAMPP control panel
- Now when you browse to the phpinfo.php file it should report that XAMPP is using the new php version. You can also place a phpinfo.php file containing in the XAMPP root catalog and browse to your site/phpinfo.php
Nessus reports the following vulnerabilities in php version 5.6.12:
- Multiple use-after-free memory errors exist related to the unserialize() function, which a remote attacker can exploit to execute arbitrary code. (CVE-2015-6834)
- A use-after-free memory error exists related to the php_var_unserialize() function. A remote attacker, using a crafted serialize string, can exploit this to execute arbitrary code. (CVE-2015-6835)
- A type confusion error exists related to the serialize_function_call() function due to improper validation of the headers field, which a remote attacker can exploit to have unspecified impact. (CVE-2015-6836)
- An flaw exists in the XSLTProcessor class due to improper validation of input from the libxslt library, which a remote attacker can exploit to have an unspecified impact. (CVE-2015-6837, CVE-2015-6838)
- A flaw exists in the php_zip_extract_file() function in file php_zip.c due to improper sanitization of user-supplied input. An unauthenticated, remote attacker can exploit this to create arbitrary directories outside of the restricted path. (OSVDB 127122)
- A NULL pointer dereference flaw exists in the spl_autoload() function in file php_spl.c due to improper sanitization of user-supplied input. An unauthenticated, remote attacker can exploit this to cause a PHP application to crash. (OSVDB 127124)
- A flaw exists in the parse_ini_file() and parse_ini_string() functions due to improper sanitization of user-supplied input. An unauthenticated, remote attacker can exploit this to cause a PHP application to crash. (OSVDB 127125)
- A flaw exists in the CLI SAPI Web Server due to improper sanitization of user-supplied input. An unauthenticated, remote attacker can exploit this to access arbitrary files outside of the restricted path. (OSVDB 127126)